Product Preview Vine Text Compiler Vine Sip Toolkit Vine Multimedia Platform Vine Active Prober Vine Firewall Card UCFRONT |
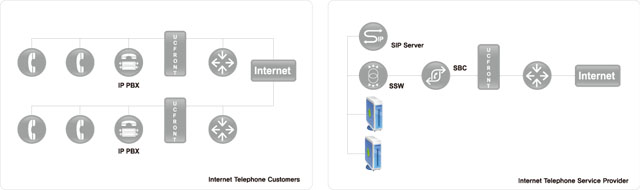
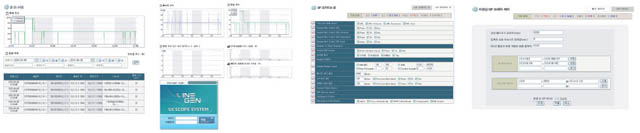
 - UC FRONT is the inspection system for on-line telephone-only firewall and intrusion detection. It is designed for flawless provision of various services by VoIP about terminal which is installed at NAT/firewall of companies and common carriers. It is made to set up SIP of VoIP and protect service based on RTP media transmission protocol. It also quickly and efficiently detects SIP flooding, DoS attack, Spam attack, charging attack, and RTP attack by using monitoring system of UC FRONT. It is the hardware all-in-one VoIp-only security device with the best functions. |
 |
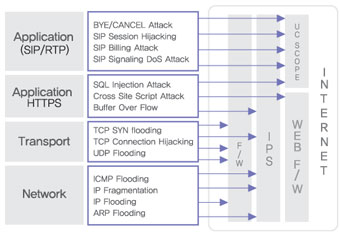
 - Set-up for SIP at network firewall and random port open issue for RTP media data -> Attacks of Flooding DoS, SQL Injection, etc. through an open port. -Attack/defense issue caused by impossibility for Header or Payload analysis on network firewall and application layer of IPS (SIP, RTP) -> the existing security device is not capable of SIP, RTP Header Field analysis (From, To, URI, Call-id, Via). - Multi-media communication by SIP and RTP prevents attack by analyzing Cross Protocol between protocols. -> Since the existing security device is not able to analyze interconnections between SIP and RTP, it is impossible to control abnormal RTP communication. - Even though the number of attack to the main protocol, SIP protocol in application service network of BCN, IMS, etc. increases, the existing security device is not good enough to detect and prevent. |
 |
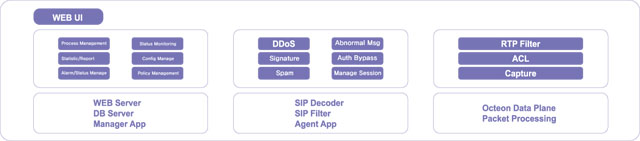
 1. Access control through SIP Firewall / Blacklist. 2. Detection and cut-off of abnormal messages through the detection engine for SIP abnormal messages. 3. Detection and cut-off of SIP Flooding DoS. 4. Detection and cut-off of spoofing message through SIP falsification detection engine. 5. Detection and cut-off of VoIP Spam attack. 6. Attack-detection and prevention through the detection engine based on SIP signature. 7. Cut-off of abnormal call through the detection engine for abnormal call flow. 8. Detection of media attack through Media Anomaly Engine for RTP 9. Supports for various set-up modes. |
  |
  |
  |
  |

